While remote software updates for medical devices have traditionally been seen as a convenient feature, the FDA now emphasizes their crucial role in safeguarding against discovered cybersecurity vulnerabilities. However, it's imperative that these updates themselves are secure; otherwise, they become potential avenues for cyber attacks.
Differentiating Secure from Insecure Software Updates
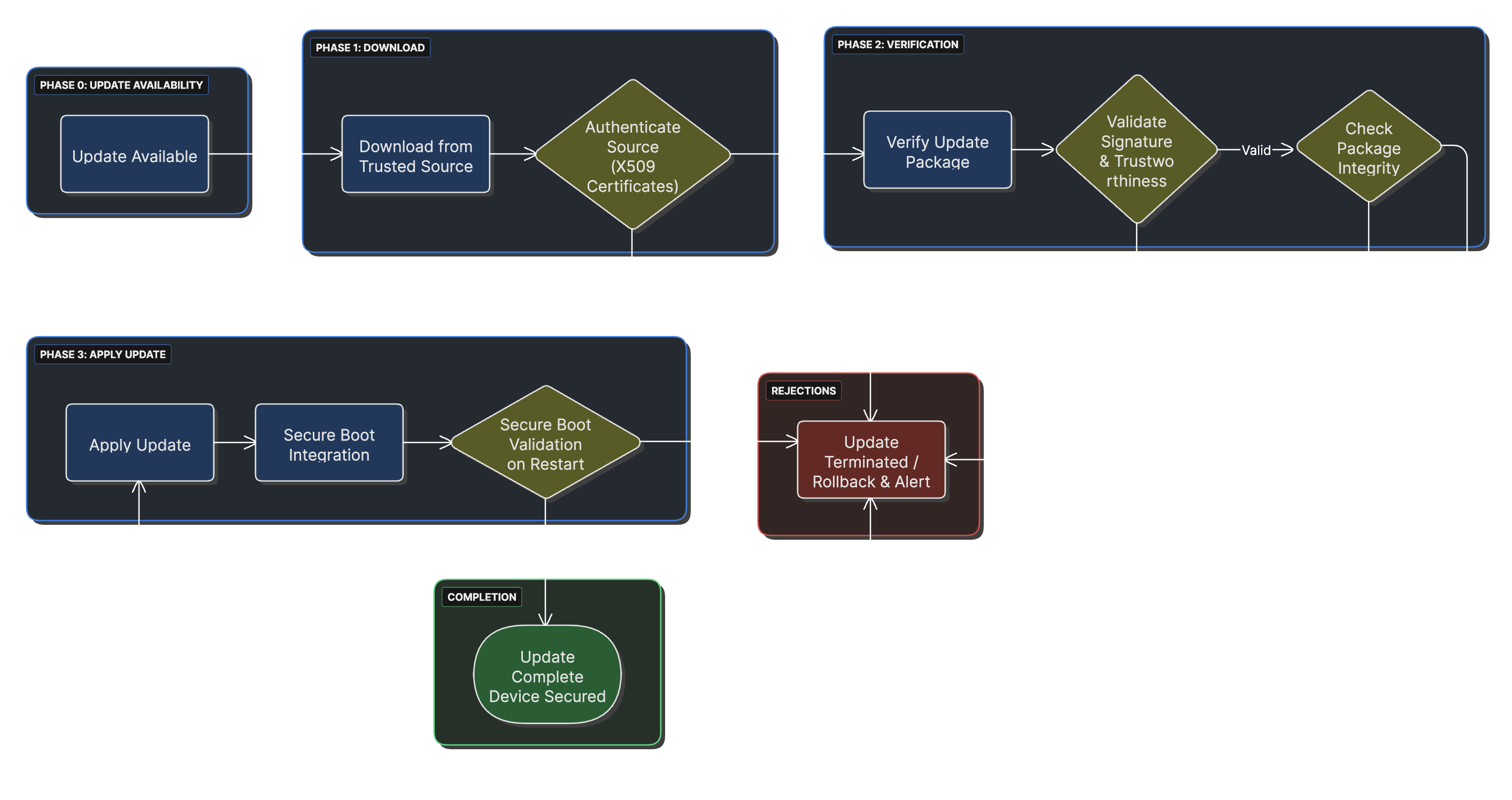
The journey towards a secure update begins with a fundamental capability known as 'secure boot'. This hardware-based feature ensures that only authorized software runs during device startup. It's paramount that no mechanism, whether in hardware or software, undermines this process.
Despite processor manufacturers often including 'back door' access for development purposes, these must be disabled in production for genuine security. The software executed during boot-up is typically stored internally within the processor, safeguarding it against modifications. While it's feasible to store boot software externally, verifying its authenticity poses challenges in smaller systems.
The selection of cryptographic authentication methods is pivotal and may hinge on available hardware and software. By combining secure boot hardware with trusted boot software, a cryptographic root of trust is established on the processor. This setup guarantees that the device powers up securely each time, allowing validation of the main software application before execution.
Steps for Secure Updates
1. Downloading from a Trusted Source
Initiating an update process begins with downloading the update from a trusted remote source. Authentication of this source is critical and can be achieved through cryptographic means, utilizing pre-provisioned information and identity details from the source.
Commonly, X509 certificates are utilized to provide attestation information, ensuring that the update source can be verified and trusted before any software is downloaded to the device.
2. Verification of the Update
Upon downloading, the update undergoes cryptographic verification to ensure its trustworthiness. This involves:
- Computing a cryptographic hash of the update
- Validating it against a provided cryptographic signature from the software builder
- Ensuring the update was produced by a trusted source
- Verifying the integrity of the update package
This verification step is crucial as it prevents malicious or corrupted updates from being applied to the device, maintaining the security and integrity of the medical device system.
3. Application of the Update
Once verified, the trusted update is applied to the device, either replacing the existing software or patching it. The new software is treated to ensure trustworthiness in subsequent power-up cycles, often involving:
- Computation of a cryptographic hash of the new software
- Secure storage of this hash for future verification
- Integration with the secure boot process
- Validation during the next device startup
Security Framework Benefits
This framework guarantees that only trusted software is executed, ensuring the system remains secure throughout the update process. The comprehensive approach provides multiple layers of protection:
- Authentication: Verifies the source of updates
- Integrity: Ensures updates haven't been tampered with
- Authorization: Confirms updates are from approved sources
- Continuity: Maintains security across device reboots
While additional considerations such as fallback mechanisms and encryption methods are important, they build upon the robust foundation established here. These may include rollback capabilities, encrypted communication channels, and secure key management systems.
Implementation Considerations
When implementing secure software updates for medical devices, several key factors must be considered:
- Hardware Requirements: Ensuring the device has adequate cryptographic capabilities
- Performance Impact: Balancing security with system performance
- Regulatory Compliance: Meeting FDA cybersecurity requirements
- User Experience: Minimizing disruption during updates
- Failure Recovery: Implementing robust fallback mechanisms
Conclusion
Secure software updates are no longer optional for medical devices—they are a critical requirement for maintaining patient safety and regulatory compliance. The implementation of a comprehensive security framework, from secure boot to cryptographic verification, ensures that medical devices can receive necessary updates while maintaining their security posture.
At Bold Type, we have decades of experience in developing and deploying secure remote software update mechanisms. Let us assist you in implementing a secure update mechanism for your next product, ensuring all software updates are executed safely and securely.
Need Help with Secure Software Updates?
Our cybersecurity experts can help you design and implement secure update mechanisms that meet FDA requirements and protect patient safety.
Get Expert Consultation